It’s possible to protect access to the system from brute-force attacks by unauthorized users, which take the form of multiple, rapid-fire attempts to guess a correct combination of login and password. With access via the SSH (Secure Shell) protocol, the system detects failed login attempts from a specific IP address, and if the number of these attempts exceeds the limit – for example, 3 failed attempts during a 60-second period – that IP address is automatically blocked for a defined period.
To ensure that access from authorized users such as the PortaOne support team will not be blocked, these IP addresses are included in the “whitelist”. A service provider can “whitelist” any specific IP addresses they don’t wish to block (the service provider’s installation IP addresses are not blocked by default).
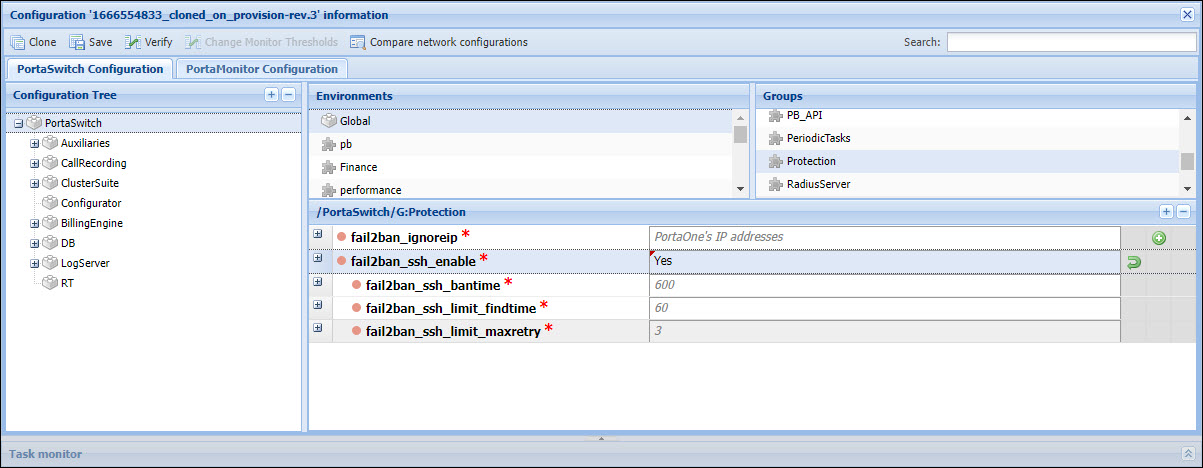
Configuration
SSH protection is enabled on the Configuration server web interface. The following parameters can be configured:
- Protection.fail2ban_ssh_enable – set Yes to enable the SSH access protection.
- Protection.fail2ban_ignoreip – this is the “whitelist” of IP addresses (by default, PortaOne’s IP addresses are added). Click Add value
 to add another specific address to the list.
to add another specific address to the list. - Protection.fail2ban_ssh_limit_findtime – specify the time frame (in seconds) to analyze the number of failed attempts from the same IP address (by, default, 60 seconds).
- Protection.fail2ban_ssh_limit_maxretry – specify the maximum number of failed SSH access attempts that are allowed before the IP is blocked (by default, 3).
- Protection.fail2ban_ssh_bantime – specify for how long (in seconds) the malicious IP addresses should be blocked (by default, 600 seconds). To block the malicious IP addresses permanently, specify the “-1” value (note that these IP addresses can be unblocked only manually, by the PortaOne support team).
Service providers can protect the system against brute-force attacks via SSH.