PortaSwitch supports a set of tools to prevent VoIP fraud, i.e. a situation where an attacker uses credentials stolen from a customer’s IP PBX or end-point and sends unauthorized voice traffic to your network.
There are two main approaches for distinguishing between the activity of a legitimate user and a hacker:
- Deviation in usage patterns.
- Deviation in the location from which the service is used (geo-IP).
The current version of the fraud protection module in PortaSwitch uses the location deviation method. This enables prevention of the majority of attacks without allowing a single fraudulent call to pass through, so there is zero loss for the service provider (or the customer). We plan to add real-time analysis of usage patterns in the next releases, to allow even better control and proactive prevention of those rare scenarios where location analysis may not yield sufficient results.
Geo-IP fraud prevention
If a hacker obtains the valid credentials of one of your customers, they can then send a call from their network using this username and password and even the identification of the SIP phone type. The only piece of information that cannot be easily changed by a hacker is their actual IP address. Although it is not always possible to determine a user’s exact location (e.g., street address) from their IP address, information regarding the country and the ISP that owns the IP address (and leases it to the end user) can be determined in the overwhelming majority of cases by using the database of IP address assignments (geo-IP database).
The key element in geo-IP fraud prevention is the assumption that, under normal circumstances, the majority of users will use your service from the same country (and the same region in that country). For instance, a VoIP user in Barcelona, Spain, connects to the Internet via DSL provided by Telefonica. Although the user’s IP address is assigned dynamically by the ISP and may change, the “location” of that address will always point back to Spain. Even if the user changes the ISP to Orange, their IP address will still refer to Spain. Usually, larger customers who use SIP trunking services are the primary target for hackers, since they have higher credit limits and are authorized to send larger numbers of simultaneous calls. By using the credentials of such a customer, a hacker can send a significant amount of traffic in a relatively short time period. Fortunately, geo-IP fraud prevention is especially accurate for this type of customers. A residential user may take his SIP phone with him to a different country while on vacation, but it is very unlikely that a company will frequently move their office (and cloud PBX) to a different country.
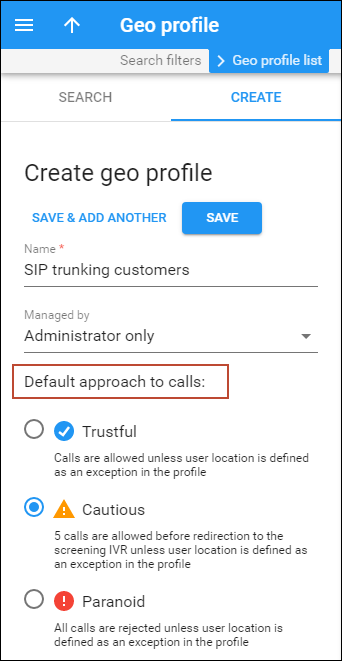
When launching the service, the service provider creates one or more Geo profiles. Each profile divides the list of all the world’s countries into three zones, depending on the call processing approach:
- Trustful – this is a country (or countries) where users intend to use the service. Service usage is allowed without restrictions.
- Cautious – these are countries where it would be unusual (but still possible, for a relatively low number of calls) for a customer to use the service without screening. Any attempt to make an outgoing call from a country on this list will be screened.
The customer must provide additional credentials to prove that the call is being made by a legitimate user.
The number of suspicious calls that can be made without screening is configured for each Geo profile. The default value is 5, but you can change it to 3 or 10. Redirecting calls to the screening IVR may start with up to an hour delay after the allowed limit of calls is reached.
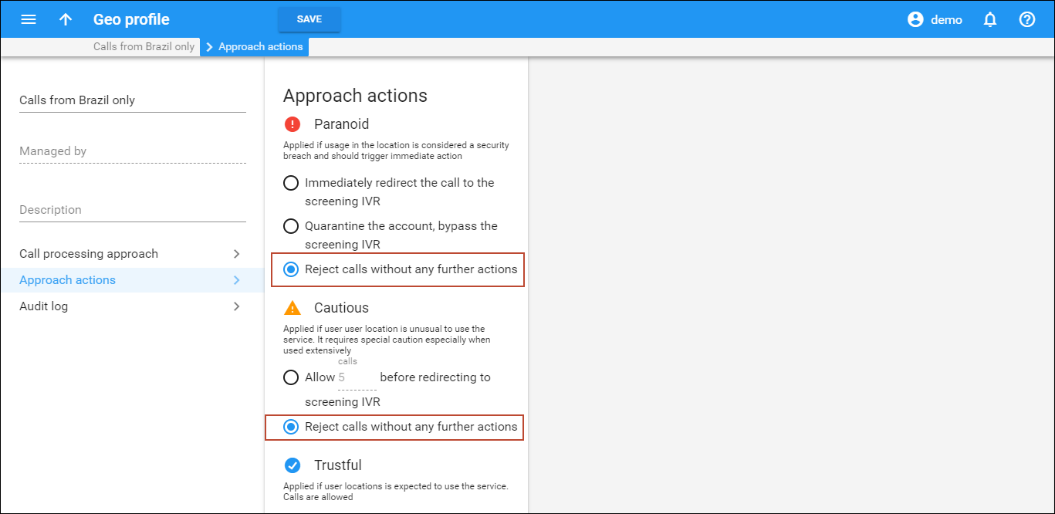
- Paranoid – any attempt to use the service from within these countries is immediately screened and treated as a potential security breach. The customer must provide additional credentials to prove that this is indeed a legitimate user.
When creating a Geo profile, an administrator chooses the default approach to calls: Trustful, Cautious, or Paranoid. The default approach is applied to calls from all user locations (anywhere in the world). The administrator can specify which countries require special handling as exceptions to the default approach. The other two call processing approaches can be applied to calls from specified countries.
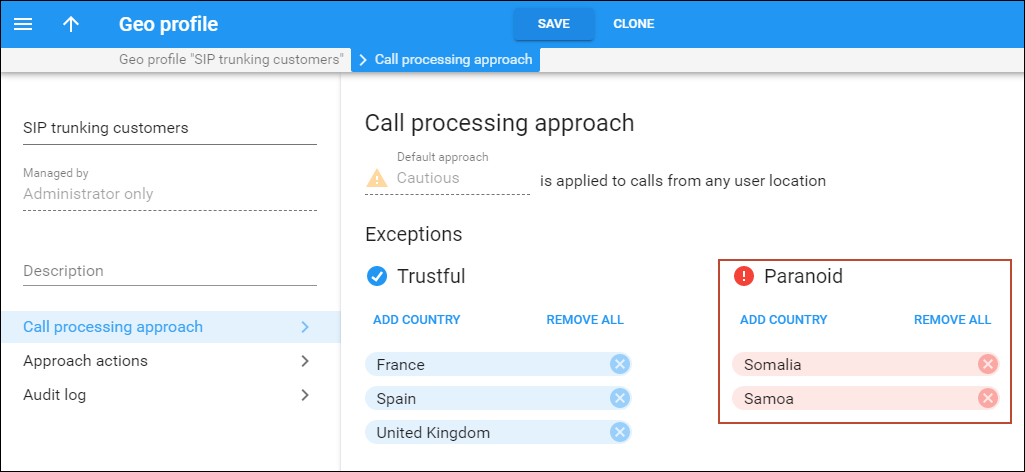
For example, Panda Telecom is going to launch a SIP trunking service in the United Kingdom, France, and Spain. To configure fraud prevention, Panda Telecom’s administrator needs to:
- Create a Geo profile and define Cautious as the default approach. Since all the CSP’s customers are based either in the United Kingdom, France, or Spain, calls from the rest of the world’s countries must be handled as “suspicious” by default.
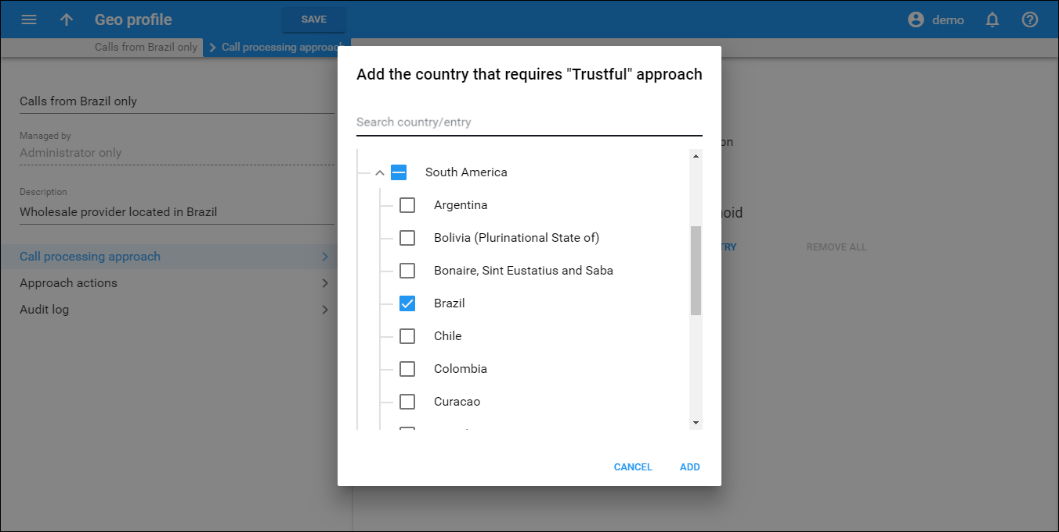
- Open the Call processing approach tab > Trustful approach and click Add country. There the administrator selects the United Kingdom, France, and Spain as exceptions. Thus, calls from these three
countries are allowed always.
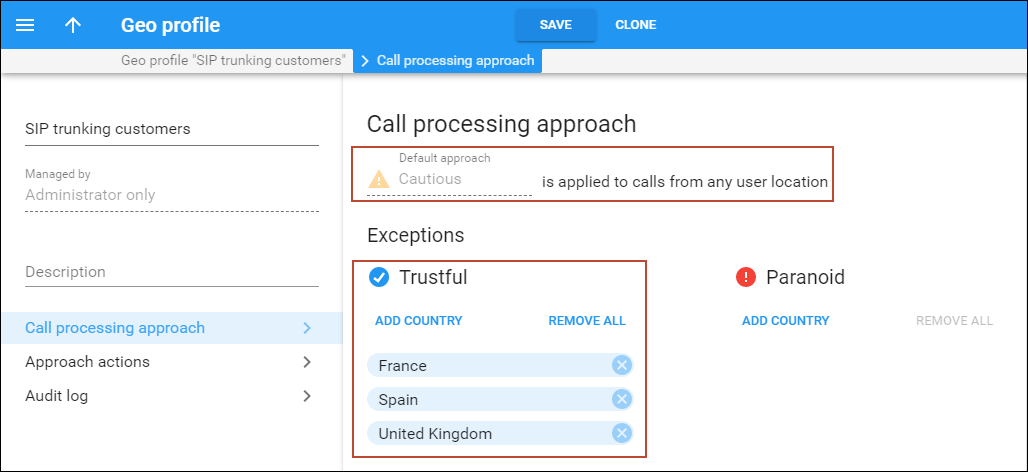
- Assign the Geo profile to the SIP trunking product.
Refer to the Fraud protection configuration handbook for more details.
Let’s say Panda Telecom finds out about increased hacking attempts from Somalia and Samoa. The administrator opens the Geo profile and adds these countries to the Paranoid approach list. Calls from these countries are considered a security breach and trigger immediate action. Actions depend on the settings specified in the Geo profile > Approach actions tab (either redirect the call to the screening IVR, quarantine the account, or reject the call without any further action).
Countries selected as exceptions are displayed in columns that correspond to each of the two call processing approaches – Trustful and Paranoid. All other countries belong to the default list – Cautious.
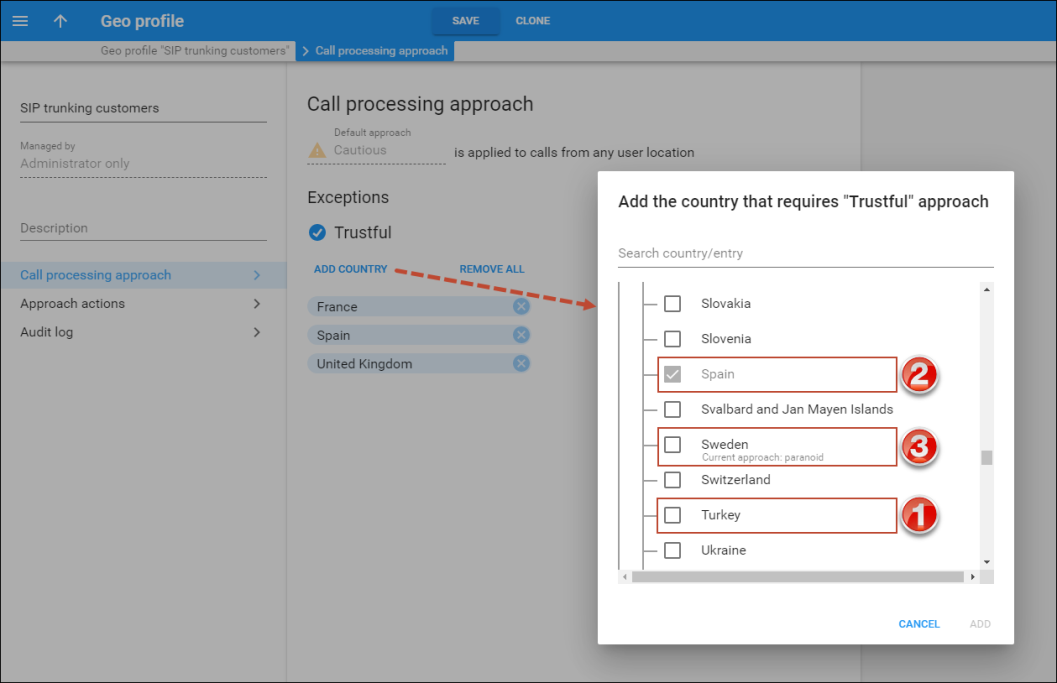
When the administrator clicks Add country, the dialog window with three types of countries opens:
- Countries without a check mark – these countries belong to the default approach list. The administrator can select them to add to the current exceptions list. For example, Turkey is on the default Cautious list now but can be selected and moved to the exceptions – Trustful list (1).
- Countries with a check mark – these countries are already on this specific approach’s list. For example, the administrator wants to add countries to the Trustful list and Spain is already there (2).
- Countries with a note that describes the current approach – these countries are already added to another exceptions list. Still, the administrator can select any of these countries and move them to the current exceptions list. For example, Sweden
was added to the Paranoid list by mistake and is now displayed with the note: “Current approach: paranoid,” so the administrator can select it to change the current approach from Paranoid to Trustful (3).
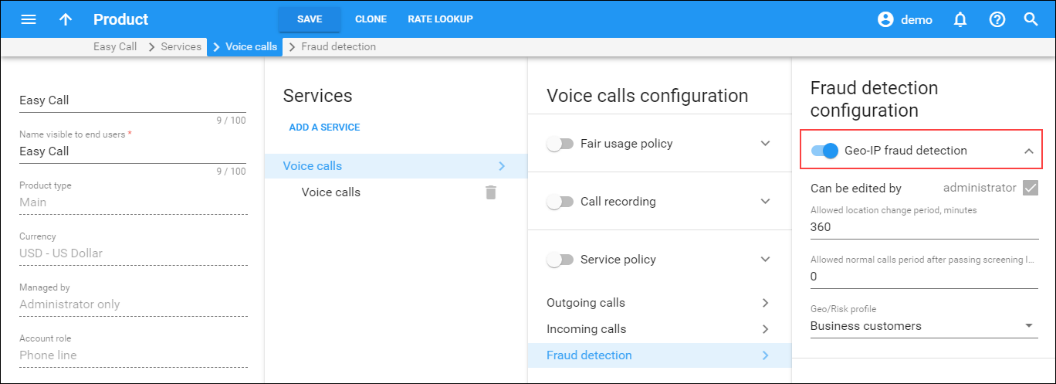
Next, Geo-IP fraud detection can be enabled within individual products, thereby allowing IP verification to be performed for all accounts using this product. This allows you to apply Geo-IP verification to business and residential VoIP products, and skip it for other products for backward compatibility or simply because it does not fit the business model. For example, this can be used for a Skype-like service, where users register and can then use it anywhere in the world.
Alerts about suspicious activities
Time is critically important when a fraudulent incident occurs. The sooner one acts, the better chance they have to mitigate possible losses.
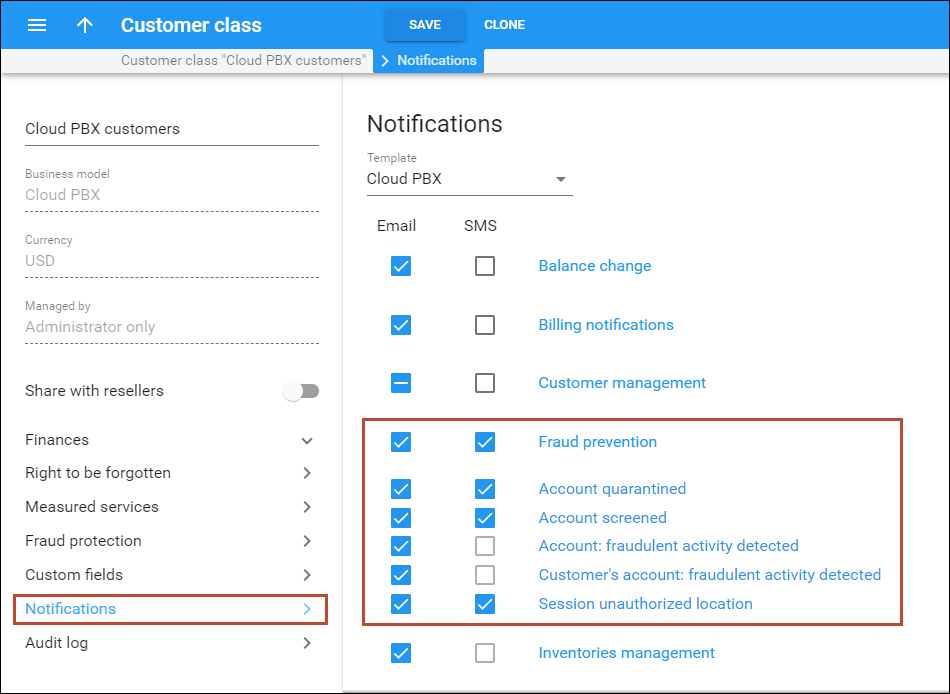
PortaSwitch provides notifications to alert customers whenever the following events take place:
- A call made from a customer’s account originates from a location known for high fraud potential and is therefore redirected to the screening IVR. The account’s status is changed to Screened.
- A call made from a customer’s account originates from a location known for high fraud potential and is therefore immediately rejected. The account’s status is changed to Quarantined.
To automatically notify your customers about these events, the Fraud prevention group of notifications must be enabled in the customer class.
When customers are promptly notified about suspicious activities, they are able to detect fraud early and take necessary protective measures to avoid possible losses.
Country blacklist
If the service provider wants to block calls originating from countries known for high fraud potential and the screening of calls by means of IVR is unacceptable, the Country blacklist functionality is the one to use.
This functionality immediately drops calls that come from blacklisted countries. While fraudulent calls are rejected, calls originating from trusted countries come through without restrictions.
Consider the following example. A customer who is a wholesale provider is located in Brazil. He wants to allow calls only originating from Brazil and deny calls originating from any other country. As many calls are sent simultaneously, screening calls by means of IVR is not optimal.
For this customer, an administrator configures the Country blacklist to include all countries except Brazil and instructs PortaBilling to deny calls from these countries by default.
After a while, a Chinese hacker hacks this customer’s account and attempts to send calls to expensive destinations. PortaSwitch detects that the account is attempting to send calls from a Chinese IP address and since China is present in the Country blacklist, these fraudulent calls are rejected, although calls from Brazil come through without any restrictions.
With Country blacklist functionality, service providers can offer more enhanced fraud protection to their customers – including the ability to consistently drop calls that originate from countries with a high fraud risk and to continue sending calls from trusted countries only.
Account attributes
The default setting for an account is “stationary,” meaning that the system expects the account to always be used in the same location. A change of country (location) is immediately considered a potential security breach. The alternative is to mark some accounts as “roaming,” in which case, the system allows for a greater number of location changes. This can be useful for customers who travel frequently and use mobile devices to communicate with clients. To reduce the amount of false alerts, a change in location will be considered acceptable in such cases. However, this will make it more difficult to detect actual fraudulent activity.
Administrators can define a time interval during which end users are not supposed to make calls from different locations by configuring the Location change allowed every option in the product definition.
For example, a location change is allowed every 240 minutes (i.e. every 4 hours). A call comes in and its location is detected as “New York.” For three days calls come from this number in New York, and then the account calls from Egypt. Merely an hour later, the same account calls from Bangladesh. Because only an hour had passed after the call from Egypt was made, the system considers the call from Bangladesh to be a potential security breach and screens it.
This restriction works independently of the geo/risk profile assigned, and applies to location changes between countries as well as within a single country. It applies to roaming and stationary end users (the latter are allowed to change location within the country specified in the Current Location option for the customer/customer site/account).
Two additional conditions may be introduced for an account:
- Screened – this means that some unusual activity has been detected for this user. An attempt to make an outgoing call will connect the user to a screening IVR, where he or she must provide additional credentials to prove that this is indeed a legitimate user.
- Quarantined – this means that after being screened, this account was unable to supply valid credentials and is still generating a large number of call attempts. In order to reduce the load on your network, all such call attempts will automatically be blocked.
Every account is assigned a “default” location. An administrator may override this country selection in order to allow a legitimate user to keep using the service in a country that is otherwise considered “unsafe.”
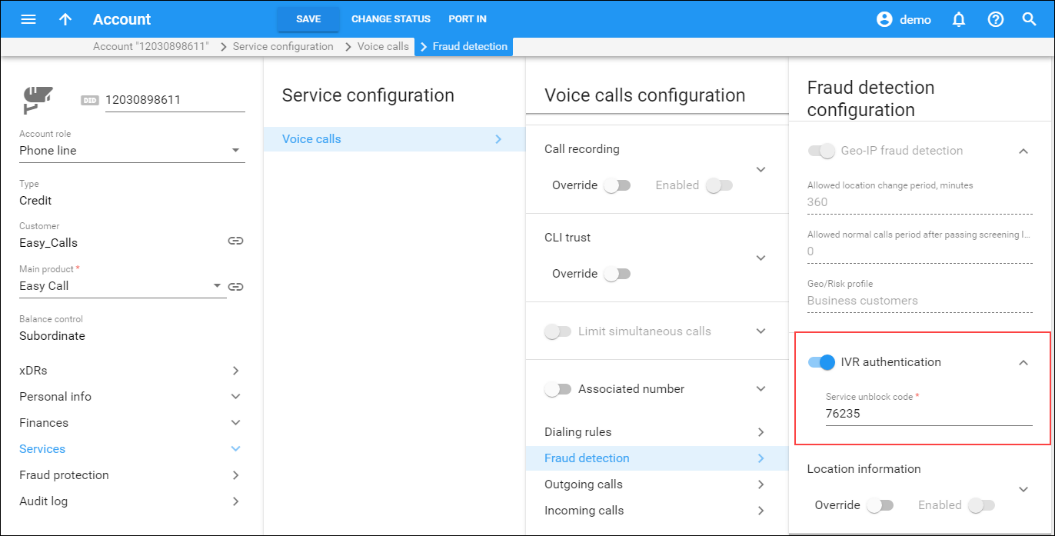
Finally, each account is assigned its own unique “service unblock” code. This is provided to the customer upon sign-up, and can be used later to confirm that a legitimate customer is attempting to make a call, therefore allowing that call from a “suspicious” location.
Call filtering
For each outgoing call, the system analyzes the combination of the account’s status, its default location, and the location from which the call is made.
- Any call from a quarantined account is immediately rejected.
- A call from a screened account is redirected to the screening IVR.
- If a call is made by a stationary account but the country of its current location does not match the default country, the call will be screened. If a stationary account does not yet have a default country assigned (e.g., a newly created account), the call is allowed only if the current country location is not on the High-risk list.
- For roaming accounts, the call is allowed if the current country location matches the default country, or if the current country location is on the No Restrictions or Suspicious list.
- In all other cases, the call will be screened.
Screening IVR
Clearly, blocking outgoing calls on any suspicion will create a negative experience for end users. A genuine customer may take his SIP phone on an overseas trip to see his family, or a businessman may need to make a very important call while transiting an airport in an “unusual” country. The screening IVR is designed to allow legitimate customers to continue making calls in situations where their activity is considered suspicious.
- The screening IVR announces that the user’s call cannot be completed because of a potential risk of unauthorized usage.
- It asks the user to re-enter the random 3-digit code he will hear. This is done to confirm that there is a live person on the line. (Hackers often use auto-dialers to test vulnerabilities in a network or generate calls to premium numbers.)
- Then the user must enter the “service unblock” code provided to him when he signed up for the service. If the unblock code is entered correctly, the system will automatically connect the user to the originally dialed number (there is no need to re-enter the number).
- If there are multiple unsuccessful attempts in the screening IVR, the account will be switched to “quarantined” status. This (along with the 3-digit “live human” verification) prevents a hacker from using a script to find the unblock code by “brute force” and continue sending traffic.