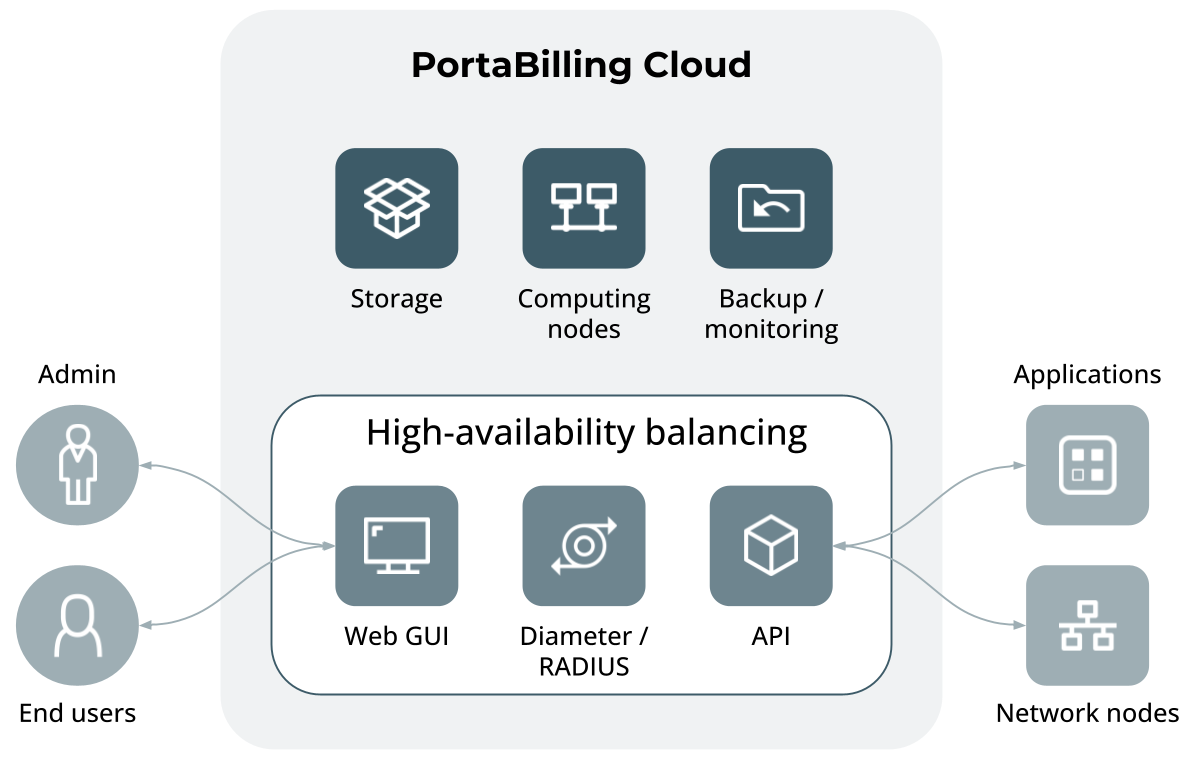
PortaOne introduces the concept of PortaSwitch as a cloud-based solution. With this solution, you do not need to purchase hardware servers and/or spend time and effort on their maintenance. Instead, you decide upon the processing capacity you require for your business, submit your request to the PortaOne Sales team and then receive a scalable, ready-to-use platform that operates in a cloud. Thus you start your business faster and speed up your payback.
The key features of the cloud-based PortaSwitch solution are:
-
Near-zero CAPEX and reduced OPEX – By deploying PortaSwitch in a cloud, you save on hardware purchases and provisioning. The cloud infrastructure is maintained by PortaOne, which drastically reduces the load on your administrative staff.
-
Reduced deployment time – You receive the platform, ready-to-use, within a day.
-
Flexible scalability – The processing capacity can be increased/decreased on demand.
-
Cloud pricing – The cloud-based PortaSwitch solution does not assume licensing. The pricing consists of a one-time set-up fee and then a recurring subscription fee that is formulated based on the number of billable xDRs processed per month. Customers interested in migrating their existing deployments to a cloud will be eligible for commercial incentives.
The cloud-based PortaSwitch platform is the solution for businesses of all sizes. Due to a reduction in deployment charges, small telcos and startups can use it to enter the telecommunications market. Large ITSPs can also use PortaSwitch to:
-
Deploy a new installation (site) in another region/country to introduce geo-redundancy and perform software upgrades with zero down-time;
-
Gradually move active customers to new installations using the Porter data transfer tool and thereby introduce a Dual Version of PortaSwitch. (For more information, please read the Dual Version PortaSwitch chapter);
-
Quickly deploy a staging system to verify new functionalities or interoperability with third-party equipment.
With PortaSwitch deployed in a cloud, you have advanced flexibility in managing your network infrastructure. Even with reduced deployment budgets, businesses of all sizes can become active players in the telecommunications market.
Site-to-site VPN for PortaSwitch deployed on the premises and in the cloud
There are several ways to deploy PortaSwitch: on the premises on hardware servers, in a cloud or as a combination of both (e.g., you disperse PortaSwitch across multiple sites for redundancy or deploy a Dual Version PortaSwitch for gradual customer migration).
For PortaSwitch installations deployed both in a cloud and on the premises, a reliable and secure interconnection must be established between these two locations. In practice, this means building a VPN that combines networks from both the cloud infrastructure and the on-premises data center. Typically, site-to-site VPNs use tunnels to encapsulate data packets within normal IP packets and forward them over public IP-based networks, using encryption to ensure privacy.
The configuration of such a tunnel involves the following:
-
set up a VPN endpoint within a cloud network;
-
set up a VPN endpoint within an on-premises network;
- make sure that both VPN endpoints freely exchange TCP/UDP traffic on ports 500 (ISAKMP) and 4500 (NAT traversal);
-
enable a tunnel between the two VPN endpoints and check the connectivity.
VPN endpoint in a cloud network
To set up a VPN endpoint in a PortaSwitch cloud network, submit a request to the PortaOne Support team. The request must include the following information:
-
a public IPv4 address for a VPN endpoint located on the premises;
-
the IP address of the private on-premises network that will be added to the VPN.
Once a VPN endpoint in a PortaSwitch cloud network is configured, you are provided with its public IPv4 address, pre-shared key and a private cloud network address.
VPN endpoint in the on-premises network
To set up a VPN endpoint in the on-premises network, either a VPN-capable device or software-based router is required (both must support standard-based IPSec encryption). Such a device/software router must be placed in the on-premises network and have a public IPv4 address assigned to it. It must also comply with the following ISAKMP policy options:
-
ISAKMP protocol, version 1;
-
exchange type: main mode;
-
authentication method: pre-shared keys;
-
encryption algorithms: AES-128-cbc, AES-192-cbc, AES-256-cbc;
-
authentication algorithm: SHA1 (also called SHA or SHA1-96), SHA-256, SHA-384;
-
Diffie-Hellman group: group 1, group 2, group 5; and
-
IKE session key lifetime: 28800 seconds (8 hours).
Additionally, support of the following IPSec policy options is required:
-
IPSec protocol: ESP, tunnel-mode;
-
encryption: AES-128-cbc, AES-192-cbc, AES-256-cbc;
-
authentication algorithm: HMAC-SHA1-96;
-
IPSec session key lifetime: 3600 seconds (1 hour); and
-
Perfect Forward Secrecy (PFS): enabled, group 5.
Please refer to https://docs.cloud.oracle.com/iaas/Content/Network/Tasks/configuringCPE.htm for useful details about a specific VPN endpoint configuration.
Enable a tunnel between VPN endpoints
Provision the public IPv4 address, pre-shared key and private cloud network address of the VPN endpoint configured in the cloud onto an on-premises device (or software router) so that a tunnel between the two VPN endpoints can be established.