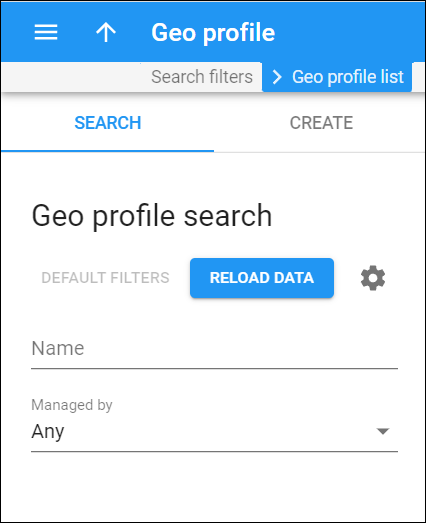
Geo profile search
Use this panel to find a specific geo profile. Specify one or more search criteria and click Apply filters. To reset search criteria, click Default filters. To refresh the search results, click Reload data.
PortaBilling automatically loads the list of geo profiles once you open the page. To disable data autoload, click Settings and clear the checkmark for the Automatically start searching upon opening the page option. When the checkmark is absent, the list of geo profiles doesn’t load until you click Apply filters.
Name
Filter geo profiles by their name. Type the geo profile name fully or partially.
Managed by
Filter geo profiles depending on whether they are managed by the administrator or a specific reseller. Select the needed option from the drop-down list:
- Any – all available geo profiles.
- Administrator only – geo profiles managed by the administrator.
- Reseller name – geo profiles managed by a specific reseller.
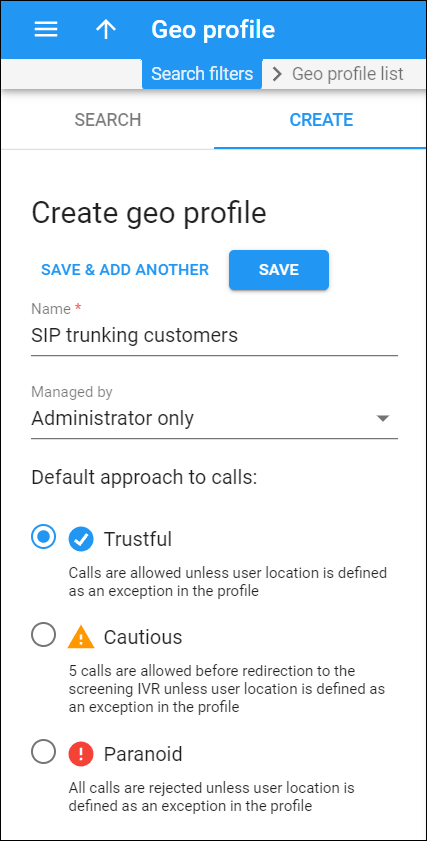
Create geo profile
Geo profile allows you to divide the world’s countries into zones depending on the call processing approach: Trustful (for expected locations), Cautious (for unusual locations), Paranoid (for high-risk locations). A call made from a specific country is allowed, screened, or rejected, depending on which zone it comes from.
To create a new geo profile, fill in the geo profile details and click Save.
Name
Type a unique name for the geo profile.
Managed by
Choose whether the geo profile will be managed by the administrator or a specific reseller.
Default approach to calls
Choose the default call processing approach. It is applied to calls from all user locations unless a user location is specified as an exception in the profile:
- Trustful – the calls are allowed.
- Cautious – a specific number of suspicious calls can be made without screening (the default value is 5, it can be changed to 3 or 10). After that, any attempt to make an outgoing call will be screened. The users will have to provide additional credentials to prove their legitimacy.
- Paranoid – any attempt to use the service is immediately screened and treated as a potential security breach.